Micro-segmentation is a fancy term, basically it is kind of next level security provided by NSX. It is well known as "Micro" because it helps us to control the traffic flow even from a vNIC.
This Micro-segmentation basically we achieve by DFW that is Distributed Firewall.
Internet is already flooded with lots of articles and documentation on it. But here I will just simplify the things, but only for those who at least knows that what is NSX :)
How to apply it-
Step 0: Login vCenter server and go to Networking and Security plugin
Step 1: Create Security groups between which you want to apply the policy. It doesn't mean that it is possible only with security groups. You can apply the firewall policy between two VMs, portgroups, IP address, SGs, vAPPs etc. it is just and example.
Step 2: Create required firewall rules and apply on security groups
Step 3: It is done
Steps explained-
Let's say I want to apply security between APP and Web VMs.
I will create two Security Groups and will name them like SG_APP and SG_Web or anything you want.
Once done.
I will create
firewall rules on the basis of below criteria.
Ex.1 - I want to block all the communication between WebServer1 and WebServer2 (Let's say I have multiple webservers)
Ex.2 - I want to allow all communication between web servers and app servers but only on port number 23
Ex.3- I want to allow all incoming connection coming toward web servers with any port number
In all the above rules, source and destination will be my
Security Groups.
For example,
Ex.1
Source - SG_Web
Destination - SG_Web
Service - Any
Ex.2
Source - SG_APP
Destination - SG_Web
Service - 23
Ex.3
Source - Any
Destination - SG_Web
Service - Any
That's it!
Above is just an example and to explain the workflow. You can anyhow manipulate the security policies and firewall as per your requirement.
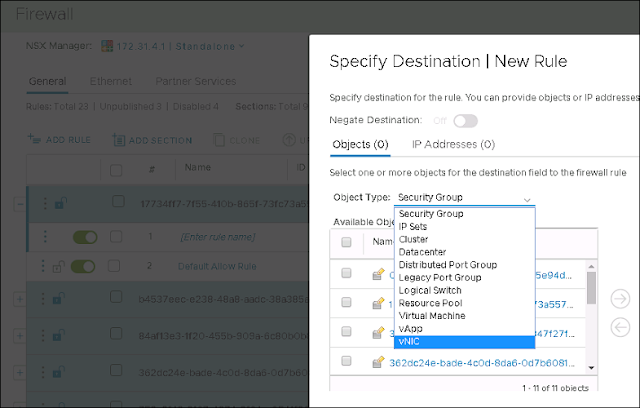
Below is an example that what can be in the source and destination list. As I said it give us option to select even a vNIC. Scroll down and you will get an idea.
Now let's think about one use case of, where we might need to select vNIC as a source or destination. I have a VM which is internet facing as well as it can access my internal network as well and of course have two vNICs (One is internet facing and second is intranet facing)
I don't want any traffic can go from my one vNIC to another vNIC.
Got an idea?
Still any doubt.Feel free to comment. I will answer it for sure..
Thank you,
Team vCloudNotes